Blockchain Explained in a Nutshell
A blockchain is the immutable chain of records which is called as Blocks, each block is secured using cryptography. Think about Blockchain as a decentralized or distributed immutable ledger for recording the history of transactions between two parties efficiently and in a verifiable and permanent way.
These records of transactions are called blocks, and each encrypted block will contain a cryptographic hash of the previous block, a timestamp and the transaction data. You now know, chaining those blocks together. Hence called a blockchain.
In the distributed ledger, a blockchain is typically managed by a peer-to-peer network collectively adhering to a protocol for validating new blocks. Once recorded, the data in any given block cannot be altered retroactively without the alteration of all subsequent blocks, which requires collusion of the network majority, which may be not possible.
Because blockchains are typically built to add the score of new blocks onto old blocks and because there are incentives to work only on extending with new blocks rather than overwriting old blocks. For example, in a blockchain using the proof-of-work system, the chain with the most cumulative proof-of-work is always considered the valid one by the network. There are a number of methods that can be used to demonstrate a sufficient level of computation. Within a blockchain, the computation is carried out redundantly rather than in the traditional segregated and parallel manner.
This is where blockchain has its advantage. While centralized data is more controllable, information and data manipulation are common. By decentralizing it, blockchain makes data transparent to everyone involved.
Every node in a decentralized system has a copy of the blockchain. Data quality is maintained by massive database replication and computational trust. No centralized “official” copy exists and no user is “trusted” more than any other. Transactions are broadcast to the network using the software. Messages are delivered on a best-effort basis. Mining nodes validate transactions, add them to the block they are building, and then broadcast the completed block to other nodes.
Blockchains use various time-stamping schemes, such as proof-of-work, to serialize changes. Alternate consensus methods include proof-of-stake. Growth of a decentralized blockchain is accompanied by the risk of node centralization because the computer resources required to process larger amounts of data become more expensive.
The objective behind the Bitcoin or Ether based Blockchain is to facilitate virtual transactions without third-party involvement.
Traditional Money transfer process:-
When you send money to another person through banks, NEFT, wire transfer, Online transfer etc. there is always involvement of central trust party which is your bank, recipient bank, PayPal etc. their role is to execute the transaction.. Also, each transaction is eligible for certain extra charges for availing the services of a trusted third party.
Have you anytime think why do we need a trusted third party involvement in traditional transactions system?
Suppose I have 1000 rupees in my account and tries to pay same 1000 rupees same time to multiple people and by the time anybody notices that I initially only had 1000 rupees but I sent out same to hundreds or thousands of different people.
The trusted central party performs precisely the below steps:
1. The sender really has the amount of money they claim to have,
2. The sender really sends that amount of money and the amount is actually removed from the sender’s possession,
3. The sender sends the amount exactly once to exactly one other person in one transaction,
4. The amount is really credited to the recipient, in the right amount, and only once.
The question now is: How can the same be achieved without a central party and without hackers and thieves?
The Bitcoin protocol proposes to achieve just that as following:
Within the Bitcoin, when I send a transaction to multiple people, I also broadcast the fact that I made this transaction to everybody. Everybody in the network is aware that I sent 1,000 Rupees to somebody. I can do this 100 times simultaneously, no worries. But then everybody in the network knows that I sent the same 1,000 Rupees 100 times to 100 different people. And then everybody in the network “votes” on which one of the 100 transactions is actually valid. In other words, if I make 100 transactions, but only happen to have the money for 1 of these transactions, only 1 of these 100 transactions is validated by a sort of “approving” mechanism. This is called “mining” in cryptocurrency terminology, more about that in the following page. The transaction is then settled, I will have paid exactly 1000 virtual Rupees (or BTC = Bitcoin) to exactly one recipient, the recipient will have received exactly 1000 virtual Rupees exactly once, and the whole transaction is entered into a public ledger (the blockchain), all without one trusted party.
Here’s what a bitcoin transaction happy path looks like.
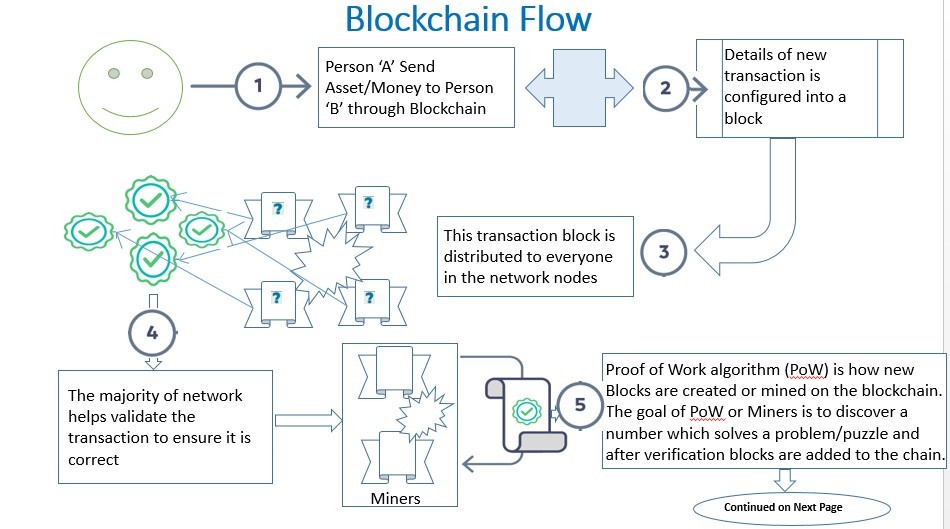
1. Person “A” initiates a bitcoin transfer to Person “B” via bitcoin network. The Person “A” must digitally sign the transaction with his private key (which is a cryptographic proof of identity). The transaction is indeed verified by the network of nodes by the public key of the sender to verify who they say they are.
2. The transaction details are recorded in a “block” and the block is announced to the peer-to-peer network for transaction verification & validation. The network verifies the longest valid block.
3. The nodes on the network move to validate the transaction block. The concept is called Proof of Work algorithm (PoW) is how new Blocks are created or mined on the blockchain. The goal of PoW or Miners is to discover a number which solves a problem/puzzle (basically involves solving a computationally intensive random math problem) and after verification blocks are added to the chain. The incentives for nodes to validate transactions is new bitcoins and associated transaction fees as a reward for ‘finding’ the new block. The process of validating transactions in a block is called bitcoin mining.
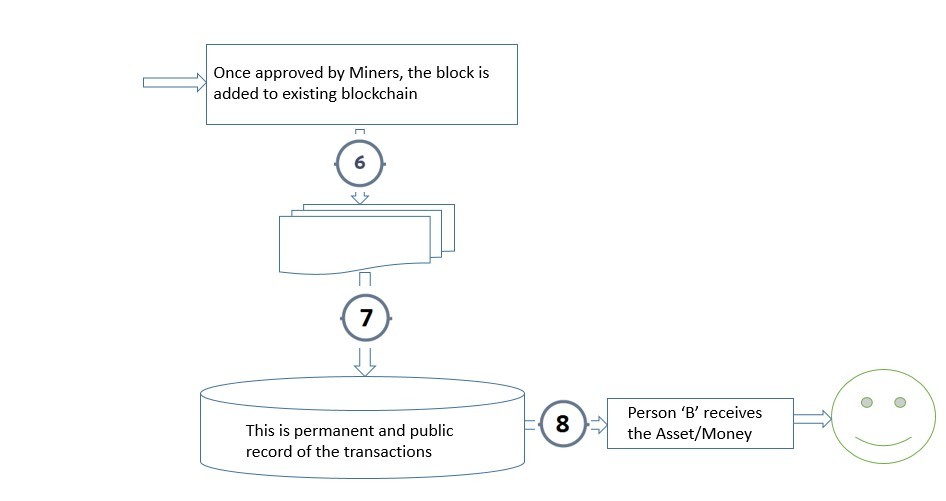
4. Every node in the network keeps a copy of all such blocks of transactions that were previously verified. This is the chain of immutable blocks, a public ledger. This chain is called the BLOCKCHAIN or Decentralised Ledger.
5. After any of the nodes successfully solves the math problem, the new transaction block is verified and the same is added to this chain by the node who successfully has solved the math first on P2P right. The winning node then broadcasts to the network that a block has been found.
6. The other nodes on the P2P network verify the winning node claims and arrive at a common consensus that the transaction has been verified and validated and the new transaction is successful. Once consensus is received each node on P2P updates their respective copy of the blockchain ledger.
7. When all of the above steps are complete, Person “A” account balance is reduced by whatever transaction amount bitcoin; and Person “B” balance increases by the said transaction amount of bitcoin.
If you see the above steps of Bitcoin transactions you will definitely agree. It becomes an immutable, chain of transaction or blocks which is indeed transparent record to everyone on the bitcoin network. This will also avoid any double-spending transactions because every transaction is recorded and broadcast to everyone and approved by consensus.
What are hash, public key and private key cryptography in Blockchain?
A hash value is the result of a hash function. Mathematically speaking, hash functions take an alphanumeric input, perform some computational math, and spit out another alphanumeric value of a predetermined length.
Let us take a simple example of generating hash keys:
The string is “My name is Ashish” and the SHA 256 generated key is
69756549E29DD21336A9C9D2344B33FF454E3ED67B0E2BA09596F09C98D96D86
For the string “My name is Ashish” and the SHA 256 generated key is
732ED05910FEFF5DB05B6A643F0A998E234A1727C05AD1AD4DDD9B9736365DED
For the string “my name is Ashish” and the SHA 256 generated key is
664BF9B71A9F7278CF0719CD81647AE552FCFDD41DF1BAA4F2943FA7DC4200CF
As you can see above, all the messages have hashes of the exact same length, regardless of the length of the input. In addition, all the messages have hashes that are entirely different from each other, even though they have the exact same meaning, and even if two of them only differ in a small and big single character.
In summary, hash functions have the following properties:
◦A given input has a precisely predictable output of a specified length.
◦Even if the input is only slightly changed, the output differs hugely.
◦The hash function or cryptographic key, it is very difficult, to predict the original input, given only the output. The degree of difficulty will depend on the strength of the encryption used.
In the blockchain transaction, a Bitcoin public address hash is the way to title the sender and the recipient of each transaction. But the beautiful thing is since everybody can publicly access the public ledger they can transparently see which sender’s as sent what transaction and to whom recipients and the whole transaction ledger.
Public Key and Private key cryptography in Generals
Suppose I have blockchain-enabled television channel locking system; I create a set of (identical) keys which are public keys that I distribute among my two children.
This keys can only be used to unlock a few of the authorized channels configured by me on my television. We will call them as public keys. And a unique key that I keep for myself, which can be used to control all the channels on television that is my private key.
So my children can only view those channels which are authorized by me by providing them identical public keys; any other channels to be open or lock will depend on my private key authorization.
Another, simple example would be I have a public and private key for my shop door lock; where the public key would be used to lock the door only with private key I can unlock the door.
Digital Keys
This is precisely how public and private key cryptography works, and the keys are created digitally.
The computerized equivalent of the above procedure is called a digital signature, where the asymmetry between private and public keys ensures the authenticity of the signature.
To summarize the process of cryptography keys in bullet points:
1. A unique pair of a public and a private key is created. The public key is created from the private key but you cannot create reverse i.e. private key from the public key.
2. The public key is visible to all on the peer to peer network.
3. The private key is kept secret by everyone on the network.
4. All the transaction in the blockchain are encrypted or digitally signed with the private key.
5. The transaction is then sent to the public address of the recipient’s.
6. The transaction can be authenticated and decrypted by anyone with the public key of the sender. This will authenticate the correct transaction.
7. It is not possible to fraud or hacks the transaction without the knowledge of the private key.
Bitcoin transaction and transfer explained:
Everyone should get a wallet to transfer the bitcoins, the wallet will help you set up your private key and you can generate one or more receiving/public addresses from your private key.
Suppose you have 10 Bitcoins in your wallet. You want to send 4 Bitcoin to somebody, So you set up the transaction, but the Bitcoin algorithm only works with whole transactions, so the algorithm will be applicable for the entire 10 Bitcoin that you have with you, You will send 4 Bitcoin to other person/recipient and the send the change of remaining 6 Bitcoin back to you by creating the public address for you.
Stay tuned for the next Article on Blockchain, I will discuss more on the Daaps and smart contract with Ethereum




Hello! I’ve been reading your blog for some time now and finally got the bravery to go ahead and give you a shout out from Porter Tx! Just wanted to say keep up the fantastic work!